Methods used for Facebook hacking and how to protect against it
Facebook is the most used social networking website used by millions of people daily.
This is the reason why everyone wants to get in this website and hack it.
The most asked question on our website and facebook fan page is “How can I hack a Facebook account?”.
There are only few methods which someone can use to hack their friend’s Facebook account.
Today I will discuss all those methods. And also will give a few tips on how to protect your facebook account from being hacked.
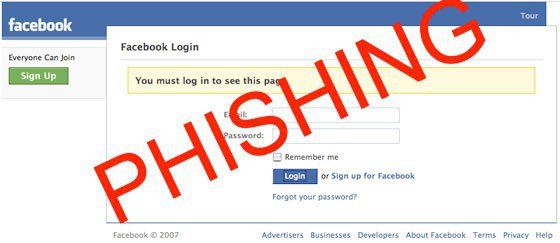
Phishing Attach
Phishing attack is the most common method of Facebook hacking. In this attack, you are sent to a website which is a copy of Facebook.
When you type your email id and password in the fields, those credentials are saved in a separate text file without giving any information to the Victim.
Protection:- Whenever you open facebook, may sure to see the URL bar. It should be https://www.facebook.com and not fakeweb.com or something else.
Keylogging
Keylogging is the easiest way Facebook accounts are hacked. Even a person with good computer knowledge can fail to notice keylogging.
The keylogger installs itself silently in the victim’s computer while another software is being installed.
Protection:- Always install software from verified publishers and well reputed websites and never install useless software like, “facebook hacker tool” or something like that.
You will never be able to hack someone’s account using those software and instead your account will get hacked.
USB Hacking
You can get all the passwords the victim saved in their computer and web browser using USB Hacking.
Protection:- Never trust unknown removable devices.
Man-In-The-Middle Attack
If the hacker and the victim are on the same network, then this attack can be performed.
The attacker acts as a default gateway between the victim’s computer and the server and gets all the information which the victim is sending to the server.
This is possible over HTTPS by establishing two independent SSL sessions, one over each TCP connection.



Comments
Post a Comment